

| Visitors Now: | |
| Total Visits: | |
| Total Stories: |
Top Secret: NSA Breaks Through Encryption
Top Secret: NSA Breaks Through Encryption
Based on recently released documents courtesy Edward Snowden, it’s evident the NSA either knows all or can get access to anything it wants by cracking all the normally used encryption technologies used on the Net as seen by the joint post from the NY Times and The Guardian.
The National Security Agency is winning its long-running secret war on encryption, using supercomputers, technical trickery, court orders and behind-the-scenes persuasion to undermine the major tools protecting the privacy of everyday communications in the Internet age, according to newly disclosed documents.
The agency has circumvented or cracked much of the encryption, or digital scrambling, that guards global commerce and banking systems, protects sensitive data like trade secrets and medical records, and automatically secures the e-mails, Web searches, Internet chats and phone calls of Americans and others around the world, the documents show.
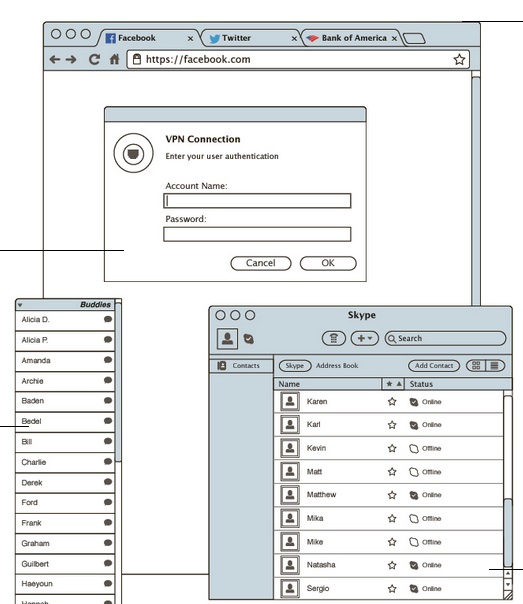
Seen below is a screen grab of the various types of private communications the NSA can crack. Click the image to learn about the different kinds of encryption we rubes use to “protect” our privacy.
Here is a blurb about Bullrun, the code word used for the top secret NSA decryption program.
A classification guide for NSA employees and contractors on Bullrun outlines in broad terms its goals.
“Project Bullrun deals with NSA’s abilities to defeat the encryption used in specific network communication technologies. Bullrun involves multiple sources, all of which are extremely sensitive.” The document reveals that the agency has capabilities against widely used online protocols, such as HTTPS, voice-over-IP and Secure Sockets Layer (SSL), used to protect online shopping and banking.
I feel better already.
Published on Nov 24, 2013
THIS IS WHERE YOU WILL FIND MORE TRUTH EXPOSED and SCANDALS UNCOVERED:
http://truth.themoneygps.com
*********************************************************************
The Money GPS by David Quintieri featuring Bob Chapman, James Turk, and David Morgan.
FREE version @ http://themoneygps.com/free
TOXIC WASTE in our Water Supply. FREE eBook:
http://fluoride.themoneygps.com
Genetically Modified Food will END Humanity. FREE eBook:
http://gmo.themoneygps.com
The Tools I Use to PREPARE for COLLAPSE:
http://amazon.themoneygps.com
*********************************************************************
Description:
Project Bullrun — classification guide to the NSA’s decryption program
Guide for NSA employees and contractors on Bullrun outlines its goals — and reveals that the agency has capabilities against widely-used online protocols such as HTTPS
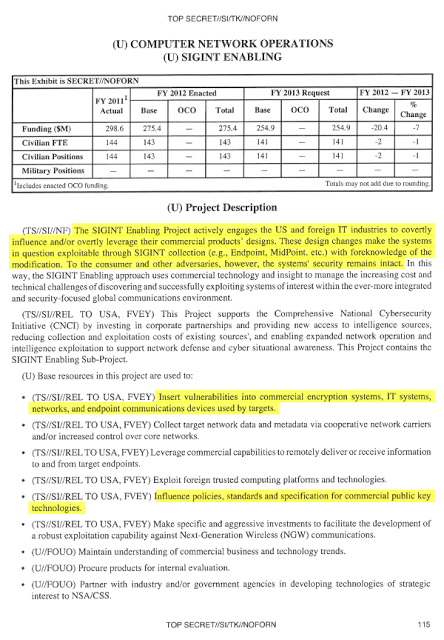
1. Project BULLRUN deals with NSA’s abilities to defeat the
used in specific network communication technologies. BULLRUN involves multiple
sources, all of which are extremely sensitive. They include CNE, interdiction, industry
relationships, collaboration with other IC entities, and advanced mathematical techniques.
Several ECls apply to the specific sources, methods, and techniques involved. Because
of the multiple sources involved in BULLRUN activities, “capabilities against a
technology” does not necessarily equate to decryption.
Sources:
http://pixabay.com/en/barcode-bar-cod…
http://www.theguardian.com/world/inte…
http://pixabay.com/en/screen-business…
You can also visit me at:
.png)
Be AWARE and be PREPARED, FEAR is not an option. Be safe everyone…





Listen you schmucks!



Remember, remember the “Enigma Machine”!!!!!
This is precisely why the sales of companies like Cisco and IBM have absolutely cratered in the global marketplace. People are saying no to companies that collaborate to make security backdoors for the NSA. Software and hardware with backdoors are not secure, so they’ve moving onto other companies/technologies that are.