| Online: | |
| Visits: | |
| Stories: |

| Story Views | |
| Now: | |
| Last Hour: | |
| Last 24 Hours: | |
| Total: | |
Kaspersky claims to have found NSA’s ‘space station malware’ Super-complex code collection had 116 spooky plug-ins
Musings On The Finite Statist Machine
Kaspersky claims to have found NSA’s ‘space station malware’
Super-complex code collection had 116 spooky plug-ins![]()
12 Mar 2015 at 08:28, Darren Pauli
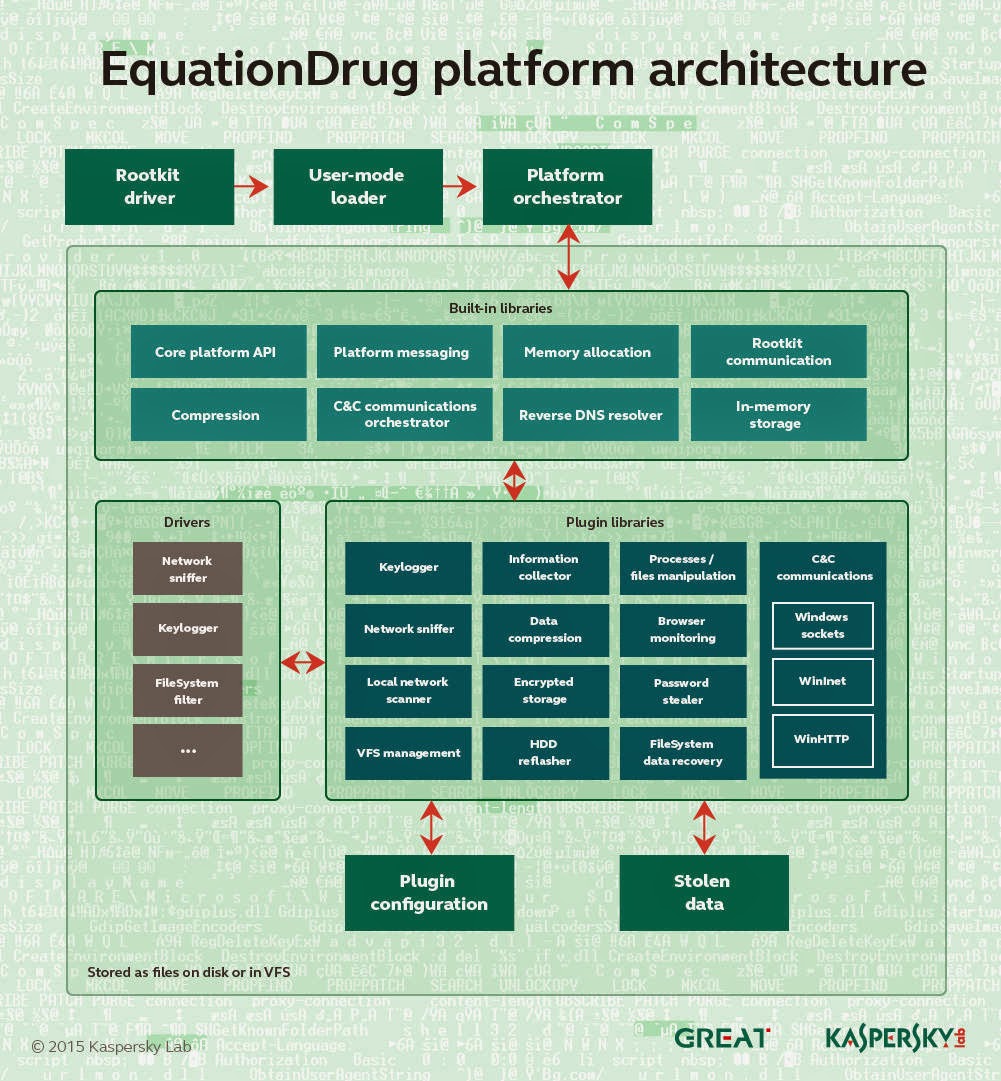
Kaspersky malware probers have uncovered a new ‘operating system’-like platform that was developed and used by the National Security Agency (NSA) in its Equation spying arsenal.
The EquationDrug or Equestre platform is used to deploy 116 modules to target computers that can siphon data and spy on victims.
“It’s important to note that EquationDrug is not just a trojan, but a full espionage platform, which includes a framework for conducting cyberespionage activities by deploying specific modules on the machines of selected victims,” Kaspersky researchers say in a report.
“Other threat actors known to use such sophisticated platforms include Regin and Epic Turla.
“The architecture of the whole framework resembles a mini-operating system with kernel-mode and user-mode components carefully interacting with each other via a custom message-passing interface.”
The platform is part of the NSA’s possibly ongoing campaign to infect hard disk firmware. It replaces the older EquationLaser and is itself superseded by the GrayFish platform.
Kaspersky says the newly-identified wares are as “sophisticated as a space station” thanks to the sheer number of included espionage tools.
Extra modules can be added through a custom encrypted file system containing dozens of executables that together baffle most security bods.
Most of the unique identifiers and codenames tied to modules is encrypted and obfuscated. Some modules capabilities can be determined with unique identification numbers. Others are dependent on other plugins to function.
Each plugin has a unique ID and version number that defines a set of functions it can provide. Some of the plugins depend on others and might not work unless dependencies are resolved.
Kaspersky bods have found 30 of the 116 modules estimated to exist.
“The plugins we discovered probably represent just a fraction of the attackers’ potential,” the researchers say.
Executable timestamps reveal NSA developers likely work hardest on the platform on Tuesdays to Fridays, perhaps having late starts to Monday.
- Modules detected in the tool include code for:
- Network traffic interception for stealing or re-routing
- Reverse DNS resolution (DNS PTR records)
- Computer management
- Start/stop processes
- Load drivers and libraries
- Manage files and directories
- System information gathering
- OS version detection
- Computer name detection
- User name detection
- Locale detection
- Keyboard layout detection
- Timezone detection
- Process list
- Browsing network resources and enumerating and accessing shares
- WMI information gathering
- Collection of cached passwords
- Enumeration of processes and other system objects
- Monitoring LIVE user activity in web browsers
- Low-level NTFS filesystem access based on the popular Sleuthkit framework
- Monitoring removable storage drives
- Passive network backdoor (runs Equation shellcode from raw traffic)
- HDD and SSD firmware manipulation
- Keylogging and clipboard monitoring
- Browser history, cached passwords and form auto-fill data collection.
Source: http://americankabuki.blogspot.com/2015/03/kaspersky-claims-to-have-found-nsas.html