| Online: | |
| Visits: | |
| Stories: |

| Story Views | |
| Now: | |
| Last Hour: | |
| Last 24 Hours: | |
| Total: | |
Professionals Suspect ISIS On A Hacking Spree pictures
Professionals Suspect ISIS On A Hacking Spree

ISIS is not willing to just sit there and listen to all of the negative things people are saying about them. They’ve taken it to the extent that their computer programmers have created malware that is allegedly able to detect insulting, anti-ISIS material posted in forums, websites, blogs and various other web channels.
Researchers from Citizen Lab in Toronto, Canada were the first to detect the malware whose sole purpose is to find those groups or people who oppose ISIS and its laws. The malware was purportedly first targeted at only one anti-ISIS group, Ar-Raqqah, and now Raqqah is being slaughtered silently for their speaking out.
This malware is usually sent via an email, Citizen Lab tells us. The sender of the email claims to be from a Canada-based group that will help support the fight against ISIS. Once the reader is convinced and chooses to join the group, they simply need to click on a link in the email and it redirects them to TempSend servers which then automatically initiates the download of a file called “slideshow.zip”.
The downloaded “slideshow.zip” file (MD5: b72e6678e79cc57d33e684528b5721bd) contains “slideshow.exe” (MD5: f8bfb82aa92ea6a8e4e0b378781b3859) which is the software itself. The file is a self-extracting executable with an icon to fool the victim into believing that it is a slideshow.
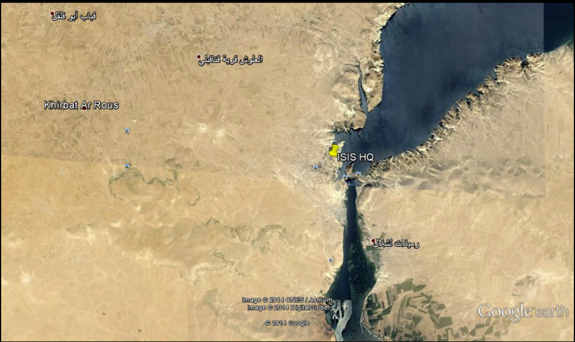
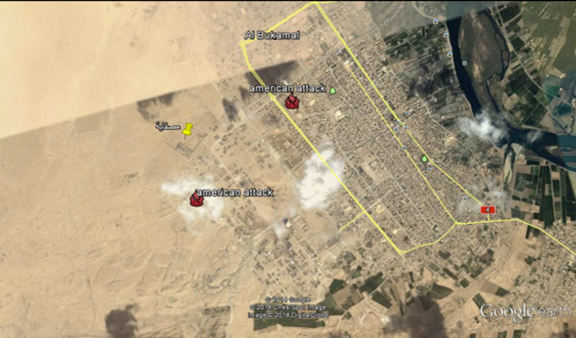
When clicked on, the file opens a slideshow of Google Earth and shows the location of ISIS Headquarters, amongst other images, including images of the US airstrikes that have been recently carried out.
However, when you look at the details of what the zip and executable files are actually doing when opened, we can see that they write and execute several other files – below are the details:
C:Users[Username]AppDataLocalTempIXP000.TMPAdobeR1.exe
C:Users[Username]AppDataLocalTempIXP000.TMPpictures.exe
AdobeR1.exe is a malicious file, while pictures.exe is a real presentation. The funny thing is when the slideshow is closed both the “AdobeR1.exe” and “pictures.exe” files delete themselves.
AdobeR1 writes a series of executable files that are programmed to collect information from within the following locations:
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpAdbrRader.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpAdobeIns.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpGoogleUpate.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpGooglUpd.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpnvidrv.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpnvisdvr.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmprundl132.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpsvhosts.exe
C:Users[Username]MicrosoftWindowsZ0xapp8T.tmpnvidrv.exe
Once they are saved, the nvidrv.exe adds itself to the Windows ‘autorun’ command located at: HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsCurrentVersionRun under name “UpdAdbreader” – creating a series of registry keys about programs that communicate:
DefaultKeyboardUserF124-5KK83-F2IV9-FDN293JIPC7-K2ODP-OFnD3-FJCC3J1K6F-DKV8J-FKVJI-GVKBU6nvisdvr.exe:
DefaultKeyboardUserF124-5KK83-F2IV9-FDN293JIPC7-K2ODP-OFnD3-FJCC3J1K4F-DKV8J-FKVJI-GVKBU4GoogleUpate.exe:
DefaultKeyboardUserF124-5KK83-F2IV9-FDN293JIPC7-K2ODP-OFnD3-FJCC3J1K3F-DKV8J-FKVJI-GVKBU3AdbrRader.exe:
DefaultKeyboardUserF124-5KK83-F2IV9-FDN293JIPC7-K2ODP-OFnD3-FJCC3J1K2F-DKV8J-FKVJI-GVKBU2nvidrv.exe:
DefaultKeyboardUserF124-5KK83-F2IV9-FDN293JIPC7-K2ODP-OFnD3-FJCC3J1K1F-DKV8J-FKVJI-GVKBU1
Posts
 Manhunt in Paris After Gunmen Storm Office And Kill 12 … January 7th, 2015
Manhunt in Paris After Gunmen Storm Office And Kill 12 … January 7th, 2015 Here’s Why Lizard Squad Keeps Attacking Xbox Live And… January 7th, 2015
Here’s Why Lizard Squad Keeps Attacking Xbox Live And… January 7th, 2015 66-Year-Old British Rock Guitarist Jailed For Taking Pa… January 7th, 2015
66-Year-Old British Rock Guitarist Jailed For Taking Pa… January 7th, 2015 The Future Is Local, The Future Is Not Monsanto January 7th, 2015
The Future Is Local, The Future Is Not Monsanto January 7th, 2015 Lead Prosecutor of Michael Brown Case Admits Witness Li… January 7th, 2015
Lead Prosecutor of Michael Brown Case Admits Witness Li… January 7th, 2015 China Attempting To Wipe Out Real Life “Pikachu” Wi… January 7th, 2015
China Attempting To Wipe Out Real Life “Pikachu” Wi… January 7th, 2015 5 Times “Obeying the Law” in America was a Terrible… January 6th, 2015
5 Times “Obeying the Law” in America was a Terrible… January 6th, 2015 US Accused of Backing Coup Attempt January 6th, 2015
US Accused of Backing Coup Attempt January 6th, 2015
COMMENTS
- anope on Here’s Why Lizard Squad Keeps Attacking Xbox Live And PSN
- WTF on Manhunt in Paris After Gunmen Storm Office And Kill 12 People
- Korbin on UK Soldiers Accused Of Gang-Raping Recruits With Objects As A Form Of Hazing
- Khenty-Amentiu on Psychologist Lists 8 Reasons Young Americans Don’t Fight Back
- jnomed on Manhunt in Paris After Gunmen Storm Office And Kill 12 People