| Visitors Now: | |
| Total Visits: | |
| Total Stories: |

| Story Views | |
| Now: | |
| Last Hour: | |
| Last 24 Hours: | |
| Total: | |
Do You Like Online Privacy? You May Be a Terrorist
http://usahitman.com/uterrorp/
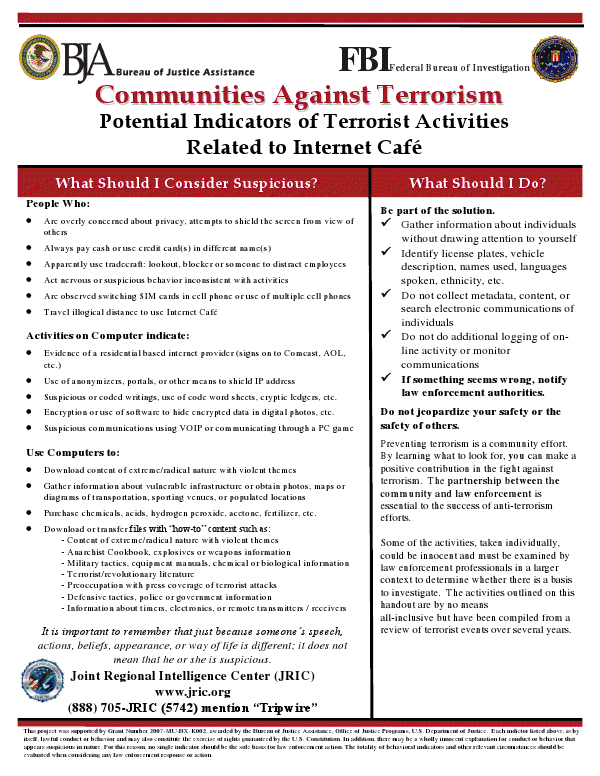
A flyer designed by the FBI and the Department of Justice to promote suspicious activity reporting in internet cafes lists basic tools used for online privacy as potential signs of terrorist activity. The document, part of a program called “Communities Against Terrorism”, lists the use of “anonymizers, portals, or other means to shield IP address” as a sign that a person could be engaged in or supporting terrorist activity. The use of encryption is also listed as a suspicious activity along with steganography, the practice of using “software to hide encrypted data in digital photos” or other media. In fact, the flyer recommends that anyone “overly concerned about privacy” or attempting to “shield the screen from view of others” should be considered suspicious and potentially engaged in terrorist activities.
Logging into an account associated with a residential internet service provider (such as Comcast or AOL), an activity that could simply indicate that you are on a trip, is also considered a suspicious activity. Viewing any content related to “military tactics” including manuals or “revolutionary literature” is also considered a potential indicator of terrorist activity. This would mean that viewing a number of websites, including the one you are on right now, could be construed by a hapless employee as an highly suspicious activity potentially linking you to terrorism.
* People Who:
Are overly concerned about privacy, attempts to shield the screen from view of
others
Act nervous or suspicious behavior inconsistent with activities
* Activities on Computer indicate:
Evidence of a residential based internet provider (signs on to Comcast, AOL,
etc.)
Use of anonymizers, portals, or other means to shield IP address
Suspicious or coded writings, use of code word sheets, cryptic ledgers, etc.
Encryption or use of software to hide encrypted data in digital photos, etc.
Suspicious communications using VOIP or communicating through a PC game
* Use Computers to:
Download content of extreme/radical nature with violent themes
Gather information about vulnerable infrastructure or obtain photos, maps or
diagrams of transportation, sporting venues, or populated locations
Download or transfer files with “how-to” content such as:
- Content of extreme/radical nature with violent themes
- Military tactics, equipment manuals, chemical or biological information
- Preoccupation with press coverage of terrorist attacks
- Defensive tactics, police or government information
- Information about timers, electronics, or remote transmitters / receivers